Over a million WordPress websites at risk because of flaw in Yoast SEO plugin
The first statement of mageewp is the Yoast SEO plugin has been updated, make sure to update your plugin.
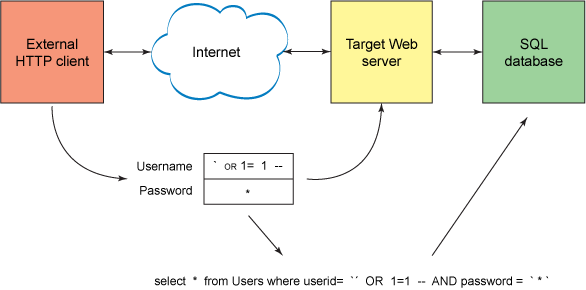
The Yoast WordPress SEO Plugin that is used by over 14 million WordPress blogs on the web has reportedly been open to an exploit where hackers can do a Blind SQL injection.
A Blind SQL Injection is a type of SQL Injection attack that asks the database true or false questions and determines the answer based on the applications response. This attack is often used when the web application is configured to show generic error messages, but has not mitigated the code that is vulnerable to SQL injection.
It can be used to insert an SQL query into the database to either extract data, modify data or delete data. It is often used to insert unwanted or unauthorized affiliate, spam links, or malware/adware on sites.
The so-called blind SQL injection vulnerability was discovered by Ryan Dewhurst, a security researcher and co-developer of the WPScan vulnerability scanner. The flaw affects versions 1.7.3.3 and older of WordPress SEO by Yoast.
In theory, exploiting the flaw requires authentication. However, since there is no cross-site request forgery (CSRF) protection, an attacker could exploit the flaw by tricking an authenticated user—like an administrator, editor or author—to click on a specially crafted link or to visit a malicious page, Dewhurst said in an advisory.
A CSRF attack involves forcing a user’s browser to execute an unauthorized action on a third-party website when that user visits a Web page controlled by an attacker. Websites must implement special protection mechanisms to prevent such attacks.
Yoast addressed the flaw Wednesday by releasing version 1.7.4 of the free WordPress SEO plug-in and version 1.5.3 of the product’s commercial variant, which was also affected.
If you are on WordPress, there is a good chance you are using this Yoast plugin. To fix the issue, upgrade to version 1.7.4 immediately. This version is documented to be a security fix based on what Ryan Dewhurst found during a security scan. The security fix says:
Security fix: fixed possible CSRF and blind SQL injection vulnerabilities in bulk editor. Added strict sanitation to order_by and order params. Added extra nonce checks on requests sending additional parameters. Minimal capability needed to access the bulk editor is now Editor. Thanks Ryan Dewhurst from WPScan for discovering and responsibly disclosing this issue.
TIPS: Yoast announced that the WordPress team actually automatically pushed an update to WordPress installs that run an older version of this plugin. So many sites running this should be automatically updated.